Local Tunneling
More Information
Local tunneling to a server
Traffic between the localhost and remote host can be tunneled via SSH connections. To establish a local tunnel on your remote server, use -L parameter when connecting and must provide
- Local port for accessing the tunneled connection
- Remote host IP/name
- Remote host port
For general usage, connect to 10.0.0.12 on port 80 on your remote host, then your local machine is able to ping or make the connection to the remote host through port 8080.
ssh -f -N -L <local-port>:<remote-host-ip-address/name>:<remote-port> <username>@<host>
# example
ssh -L 8080:10.0.0.12:80 username@hostNow if you go to your browser/curl to localhost:8080, you are able to see the content that hosted at 10.0.0.12:80.
| Parameters | Description |
|---|---|
| -f | let SSH go into the background before executing |
| -N | does not open a shell or execute a program on the remote side |
| -L | establish a local tunnel to your remote server |
If you want to terminate the background connection, you have to find the PID and kill it.
ps aux | grep <local-port>
kill <process-id>Output
1001 5965 0.0 0.0 48168 1136 ? Ss 12:28 0:00 ssh -f -N -L 8888:your_domain:80 username@remote_host
1001 6113 0.0 0.0 13648 952 pts/2 S+ 12:37 0:00 grep --colour=auto 8888kill 5965Local tunneling local network
You can tunnel remote host local network to your local. Here is the animation diagram of the local network web server and common SSH server.
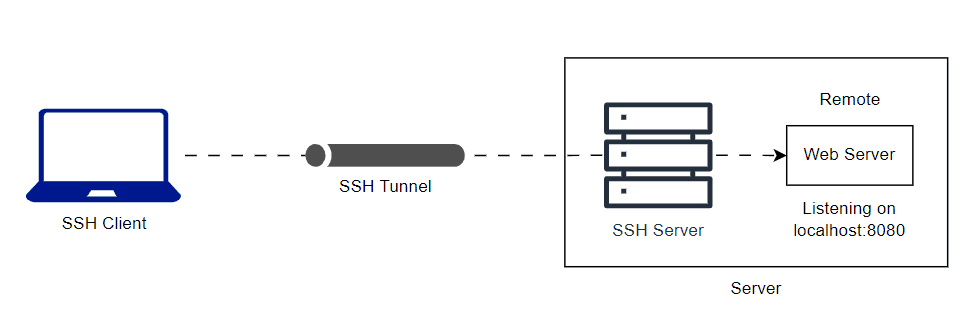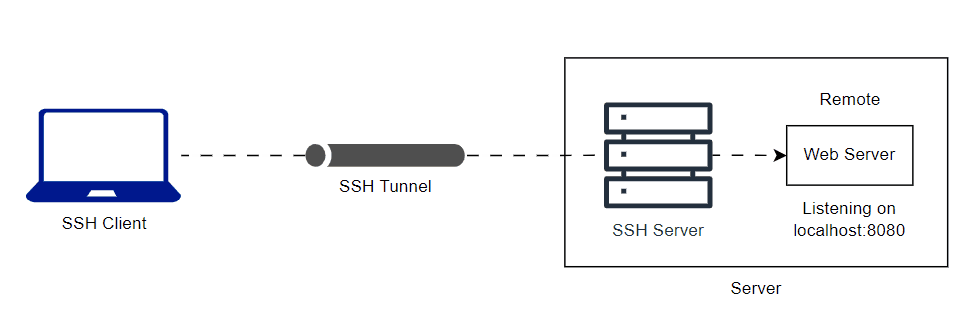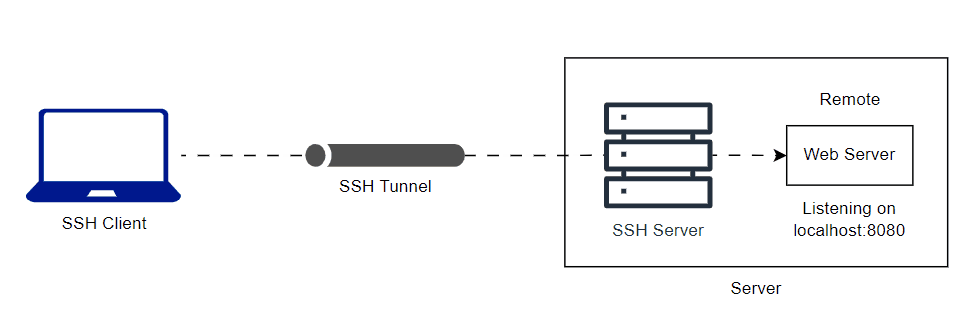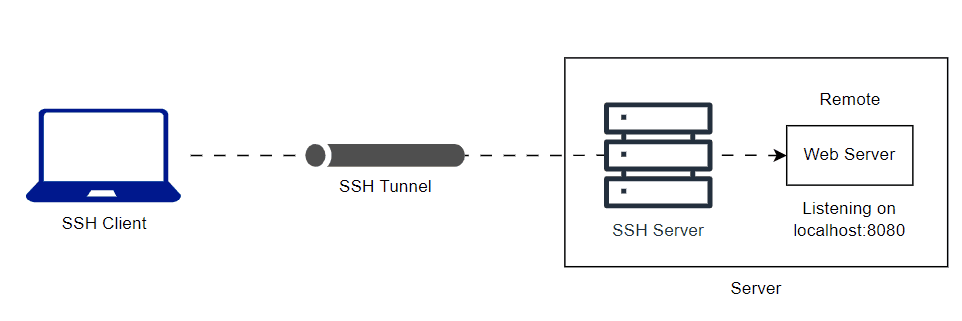
ssh -L 8080:localhost:8080 user@serverLocal tunneling private network
You can tunnnel remote host private network to your local. Here is the animation diagram of the private network web server and common SSH server.
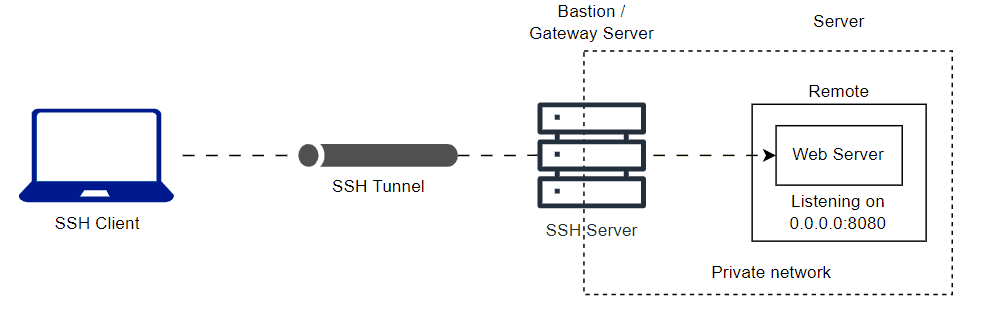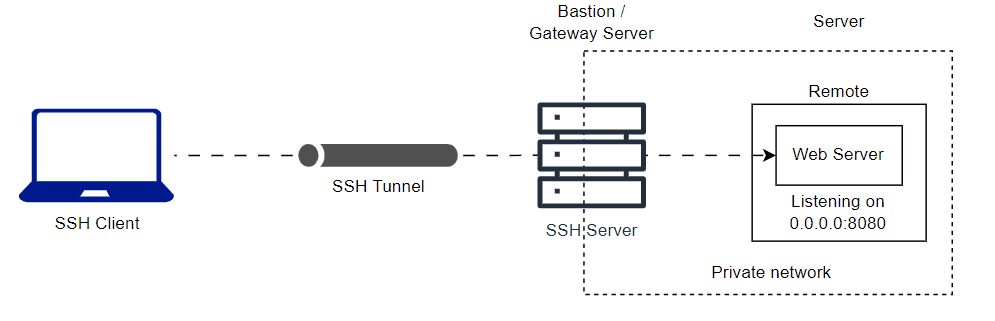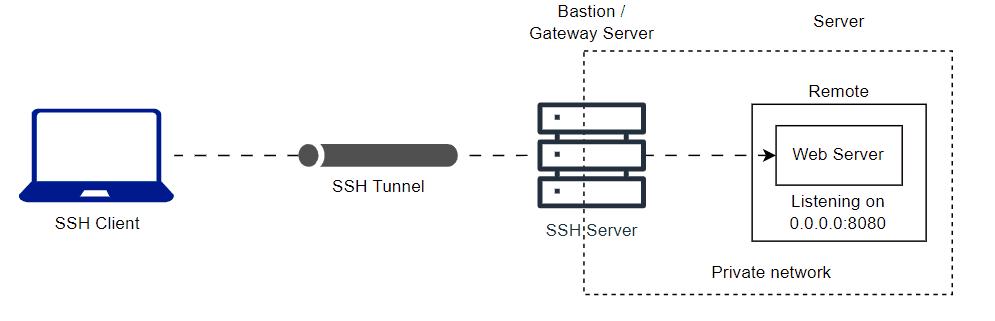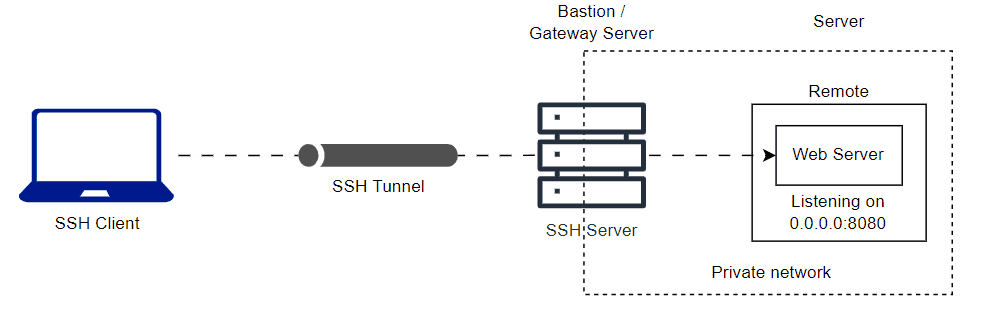
ssh -L <local-port>:<server-ip-address>:<server-port> <username>@<bastion-server-ip-address>
ssh -L 8080:10.0.0.12:8080 user@bastionLast updated on